❮ 2024-01-06
Iris CTF Writeups
CTF Writeups for IrisCTF
Jeopardy CTF with local group from Braunschweig.
Challenges I solved
skats network history - Networks
Wireshark pcap with encrypted wifi transmission only, plus a Linux filesystem. And an ssl keyfile.
You could find the WIFI's password inside it:
[wifi]
mode=infrastructure
ssid=skatnet
[wifi-security]
auth-alg=open
key-mgmt=wpa-psk
psk=agdifbe7dv1iruf7ei2v5op
There was also a firefox profile with a link to a pastebin url in the history file, but the link 404s.
Generate PSK here: https://www.wireshark.org/tools/wpa-psk.html
Open wireshark and add key to IEEE802.11 Protocol.
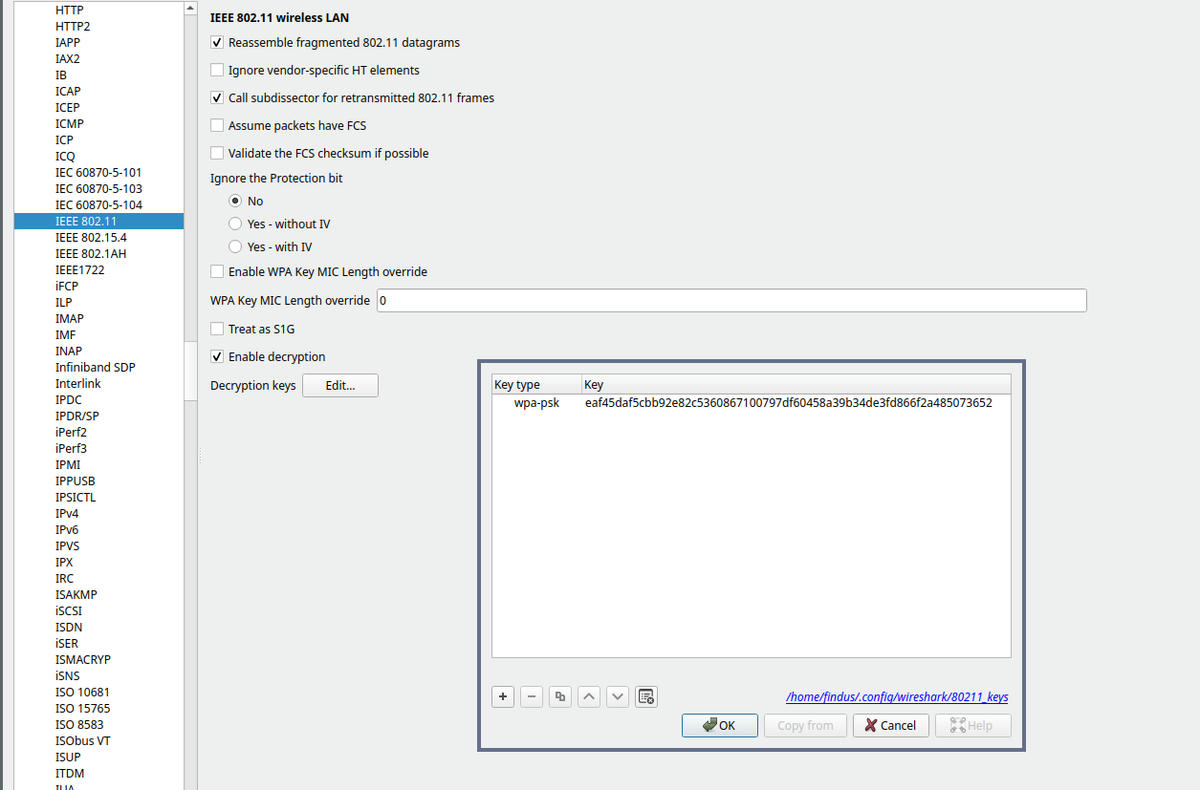 Wireshark PSK
Wireshark PSK
Decrypt TLS Traffic with the keyfile, also possible with Wireshark.
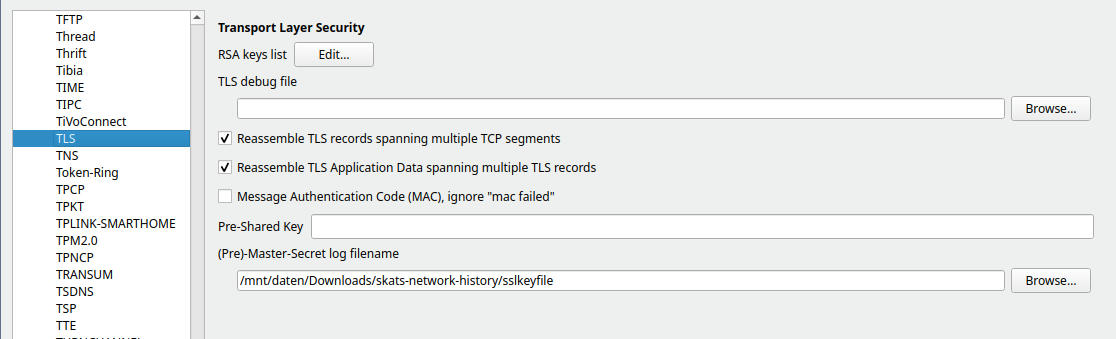 Wireshark TLS
Wireshark TLS
Filter to http2 traffic and search for the pastebin http request you know from the firefox profile
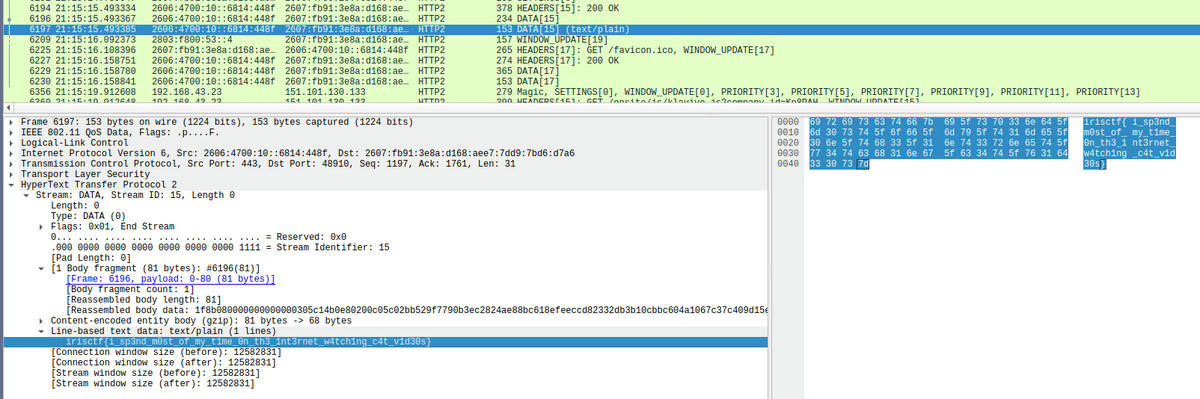 Wireshark HTTP
Wireshark HTTP
Name that song 3 - Misc
.kt file is Klystrack tracker file
Found the song on the Klystrack Discord server:
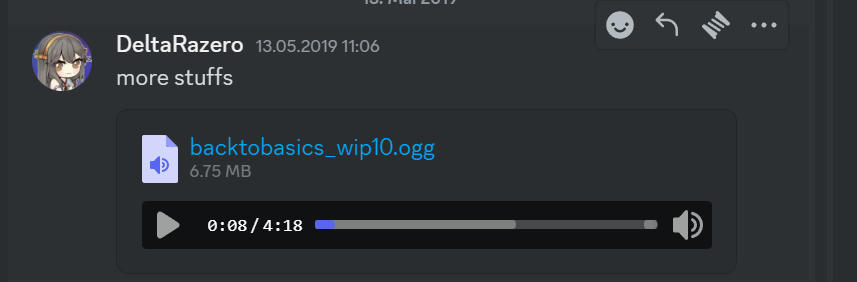 Discord
Discord
Creator has soundcloud
also Battleofthebits account if you google their name:
Name that song 4 - Misc
Crazy challenge to find a song, mostly chiptune stuff. Download was a .tap file, quick google search revealed it can be opened with a tool called "Beeopola"
Beepola can load the tap file, I just searched for songs created with beepola and tritone on Battleofthebits.
skat’s SD Card - Forensics
SD Card image with linux filesystem
- User has firefox user profile:
- Pastebin with rsa key:
- ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCv/ZnNTSNTzOsd2hiC6UnOu7p+cb7JrramwXKh0Mnu - Pastebin.com
Bash History:
I got stuck trying to recover the deleted folder, as I thought that we can recover it with tools like testdisk.
The solution was to crack the ssh keys password, with a recent version of john you could crack the passowrd in seconds (rockyou), the password was ..... password.
Cloning the repo and doing "git grep ctf $(git rev-list --all)" got us the flag.
Secret FBX - Misc
We got second blood on this challenge
 🩸🩸
🩸🩸
3D Model that was encrypted, we had to somehow open it in Blender to get the Flag.
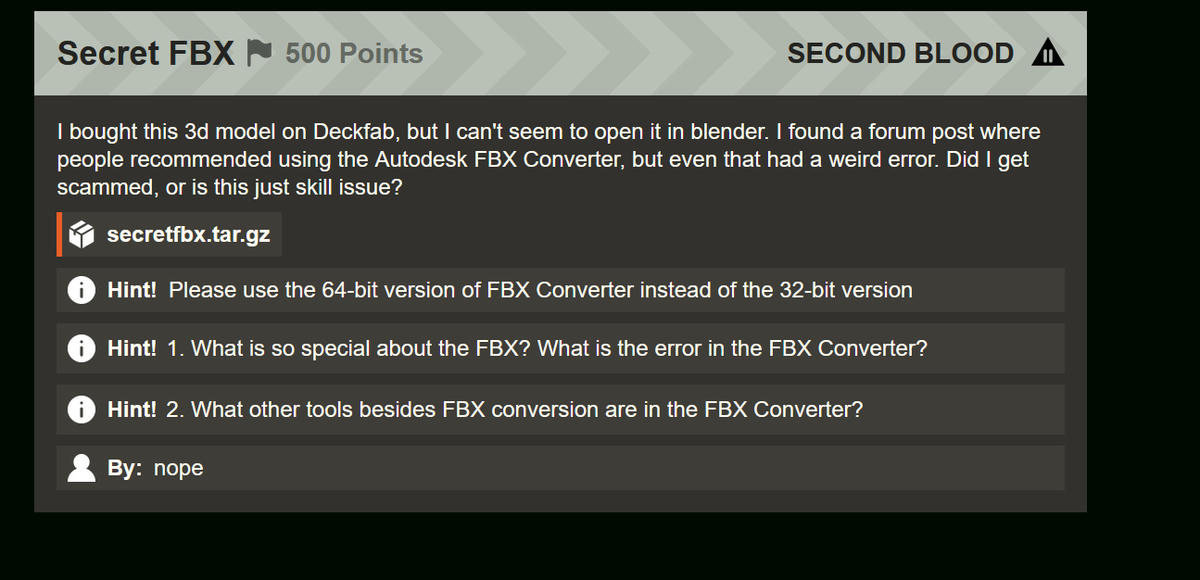
Loading the Model in the official FBX converter, but the import failed, but we could read basic metadata, one was kinda ... sus:
 SUS
SUS
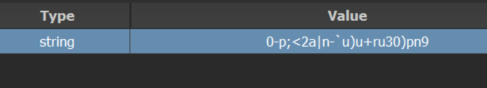
What the converter did not reveal: The FBX Api has some kind of password protection, but the converter tool just doesn't load the model at all instead of asking for a password ... weird.
According to the API-Doc the SDK is capable of decrypting encrypted models.
So I installed the FBX SDK Toolchain on my PC and started an example program that has a password prompt:
 SDK
SDK
A Team member took a look at the SDKs source code in Ghidra, and found out that there is some logic to transform the NodeIDs Value to a password:
 Ghidra
Ghidra
He reversed the algorithm and so we got the first part of the flag:
#!/usr/bin/env python3
= b
=
=
in , in
+=
+=
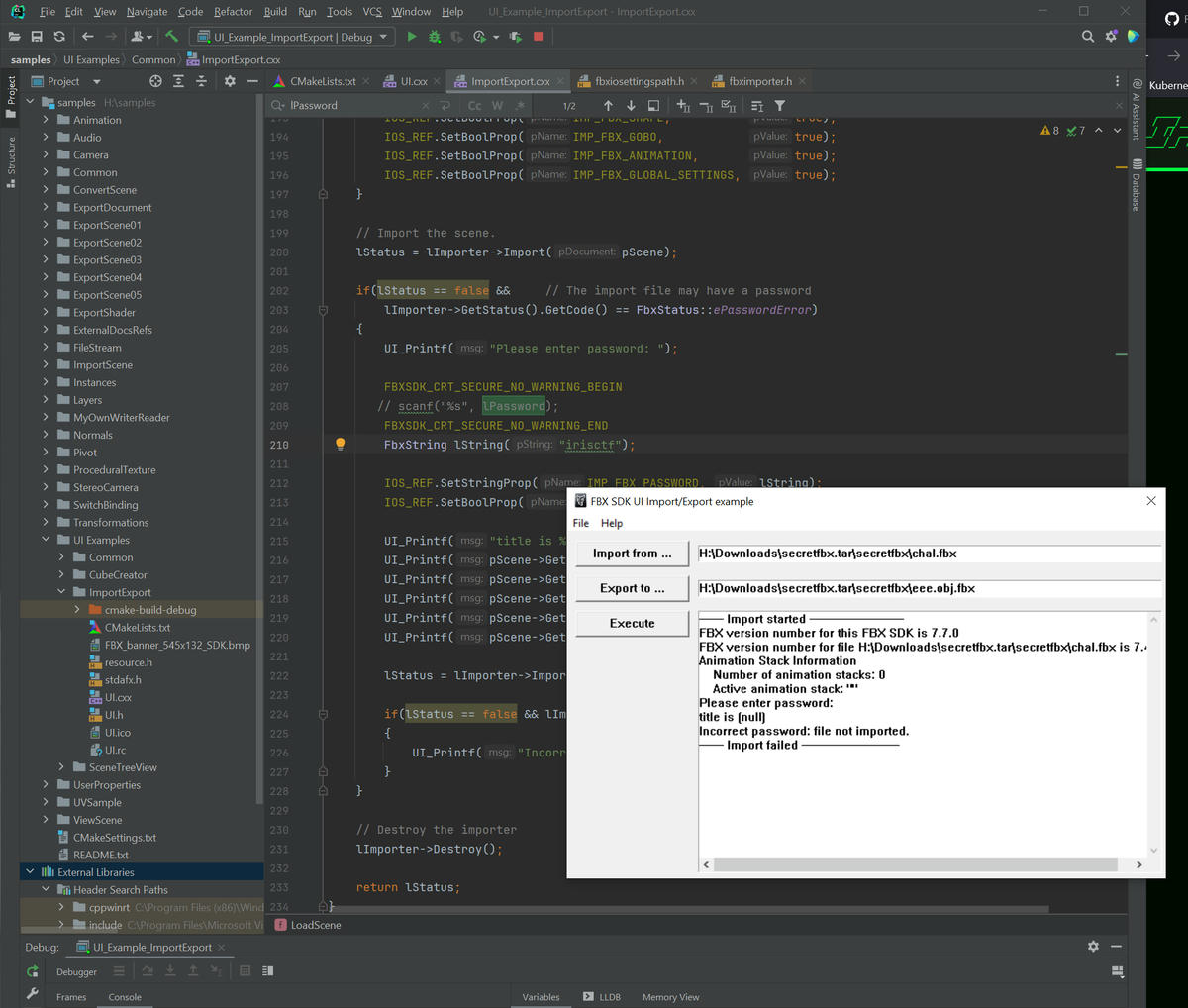
This part of the flag was the password to decrypt the 3D model:
 Decryption works with that password
Decryption works with that password
Importing the file in Blender got us the second part of the flag:
 Decryption works with that password
Decryption works with that password